What is OAuth and How it works
OAuth is an open-standard authorization protocol which provides secured access. OAuth doesn’t share password but instead uses authorization allows to approve one application interacting with another on your behalf without giving your password.
Here Let’s see the OAuth in detail with Social Sign On.
Scenario Based Explanation:
Shan uses his Google account to authenticate himself with Spotify and listen to music seamlessly without needing a separate set of credentials.
Here’s step-by-step guide for Shan to listen to music in Spotify using Google authentication via OAuth
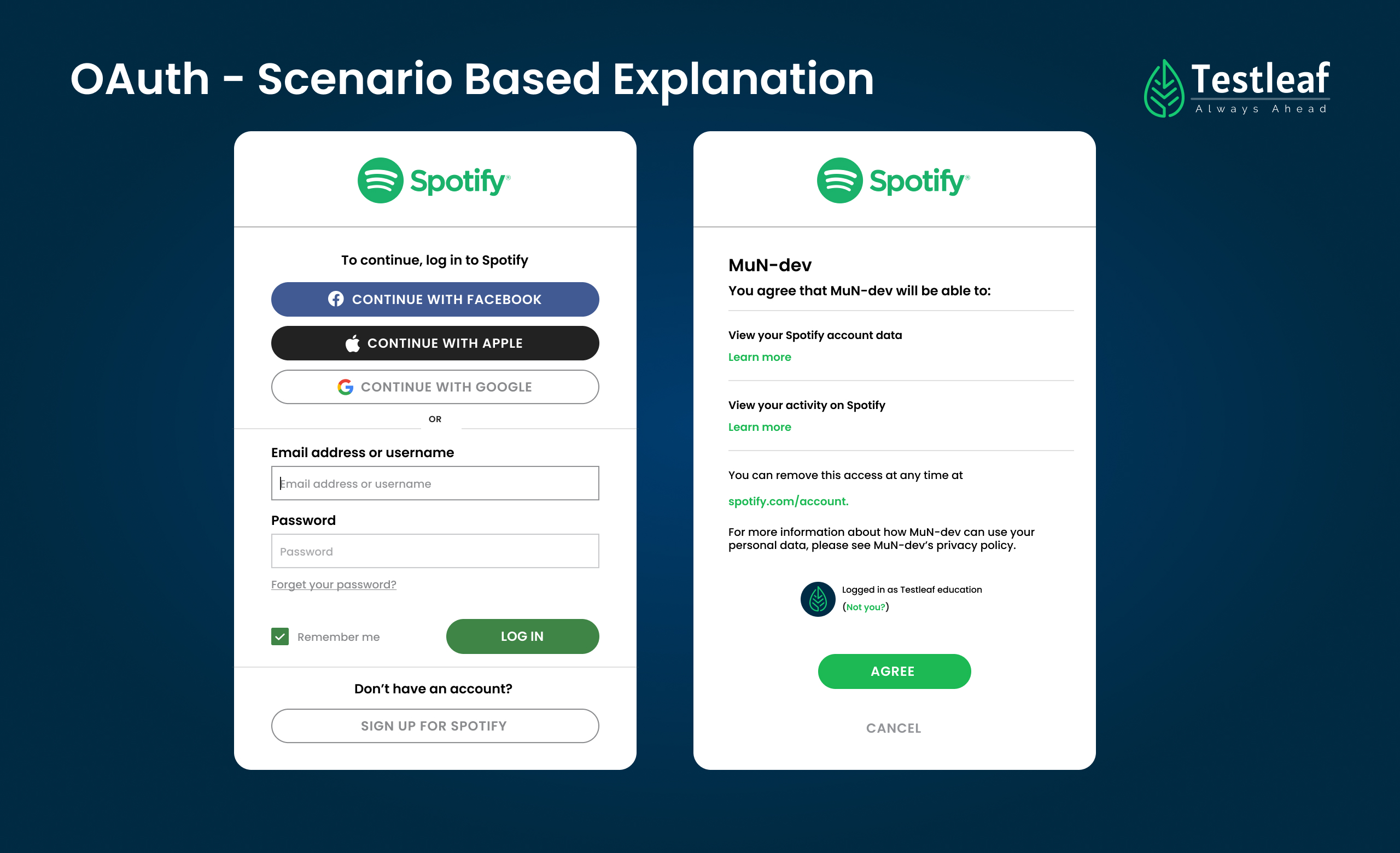 1) Login with Google Account:
1) Login with Google Account:
After Login with Google account, Shan will be redirected Google OAuth Screen where Google asks for permission to share certain information with Spotify
2) Redirect to Google OAuth:
Shan reviews the permissions requested by Spotify and grant permission for accessing the information
3) Grant Permissions:
Shan clicks “Allow” to grant Spotify permission to access the requested information from Google
4) Redirect to Spotify:
Google redirects Shan back to Spotify with an authorization code
5) Issue Access Token:
Spotify’s server verifies the authorization code sent with (client ID and client secret) and issues an access token for Shan
6) Access Spotify music library and Play list:
Spotify uses the access token to authenticate Shan’s requests to access his music library and stream music
Understanding OAuth(Technically): Beyond the Basics
OAuth, in essence, facilitates secure third-party access to user resources without divulging credentials. The process involves authorization and token exchange, ensuring a robust layer of security. Unlike traditional methods, OAuth allows users to grant limited access, enhancing control over their sensitive data.
Key Components of OAuth
Authorization Server
The authorization server plays a pivotal role in OAuth, authenticating the user and granting access tokens. This component acts as the guardian, ensuring that only authorized entities gain entry.
Resource Owner
In the OAuth dance, the resource owner is the end-user who possesses the data. Understanding their role is critical in comprehending the secure flow of information.
Client
The client, often an application seeking access, must undergo a rigorous authentication process. This step ensures the legitimacy of the requesting entity.
Access Token
The coveted access token is the golden key that unlocks the resource vault. It serves as a temporary authorization, granting limited access to predefined user data.
OAuth in Action: A Step-by-Step Guide (Technical)
User Initiates the Process:
The OAuth journey begins when a user initiates access to their protected resources, triggering the authorization server.
participant User
participant Authorization Server
User->>AuthorizationServer: Initiate Access
Authorization Grant Request:
The client, seeking access, sends an authorization grant request to the authorization server.
participant User
participant Authorization Server
User->>Authorization Server: Grant Request
User Authentication:
The authorization server authenticates the user, validating their credentials before proceeding.
participant User
participant Authorization Server
User->>Authorization Server: Authenticate
Access Token Issuance:
Upon successful authentication, the authorization server issues a time-bound access token to the client.
participant User
participant Authorization Server
Authorization Server->>User: Issue Access Token
Resource Access:
Armed with the access token, the client gains limited access to the user’s protected resources.
participant User
participant Client
User->>Client: Allow Limited Access
OAuth Best Practices
To leverage OAuth effectively, adhere to these best practices:
Token Expiry Policies:
Implement strict token expiry policies to minimize security vulnerabilities.
HTTPS Usage:
Always use HTTPS to encrypt data during token exchange, mitigating the risk of eavesdropping.
Client Validation:
Thoroughly validate and authenticate clients to prevent unauthorized access attempts.
Conclusion
In conclusion, OAuth stands as a linchpin in modern authentication, offering a secure and efficient means of accessing user data. By understanding its components, implementation, and best practices, you can navigate the intricate landscape of OAuth with confidence. Stay secure, stay authenticated.
Author’s Bio:

As CEO of TestLeaf, I’m dedicated to transforming software testing by empowering individuals with real-world skills and advanced technology. With 24+ years in software engineering, I lead our mission to shape local talent into global software professionals. Join us in redefining the future of test engineering and making a lasting impact in the tech world.
Babu Manickam
CEO – Testleaf